Editor’s Note – As the days roll into the new year, each seems to shed new light on the activities of the NSA. The excuses no longer hold water, and we all know of the lies and secrecy. Now two different courts disagree on the legality of the NSA activities but you can be sure of one thing, there is no more privacy. In the following articles you will find the latest revelations beginning with a report from a German publication, Der Speigel.
Next we see that NSA employs a mighty toolbox and ancillary effects on our daily lives. Then we see how the NSA hacks your I-Phone followed by a critique of the NSA Review report.
German magazine claims NSA hacking unit uses powerful methods to obtain data
From Fox News
A German magazine, citing internal documents, claims the NSA’s hacking unit uses James Bond-style spy gear to obtain data, including intercepting computer deliveries and outfitting them with espionage software.
Der Spiegel’s revelations relate to a division of the NSA known as Tailored Access Operations, or TAO, which is painted as an elite team of hackers specializing in stealing data from the toughest of targets.
Citing the internal documents, the magazine said Sunday that TAO’s mission was “Getting the ungettable,” and quoted an unnamed intelligence official as saying that TAO had gathered “some of the most significant intelligence our country has ever seen.”
“During the middle part of the last decade, the special unit succeeded in gaining access to 258 targets in 89 countries — nearly everywhere in the world,” the report said. “In 2010, it conducted 279 operations worldwide.”
Der Spiegel said TAO had a catalog of high-tech gadgets for particularly hard-to-crack cases, including computer monitor cables specially modified to record what is being typed across the screen, USB sticks secretly fitted with radio transmitters to broadcast stolen data over the airwaves, and fake base stations intended to intercept mobile phone signals on the go.
The NSA doesn’t just rely on the Bond-style spy gear, the magazine said. Some of the attacks described by Der Spiegel exploit weaknesses in the architecture of the Internet to deliver malicious software to specific computers. Others take advantage of weaknesses in hardware or software distributed by some of the world’s leading information technology companies, including Cisco Systems, Inc. and China’s Huawei Technologies Ltd., the magazine reported. (Read the rest here.)
More Editor’s Notes – The following story, also originating at Speigel, we see just how intrusive the NSA can be, and its not just hacking. Have you had weird things happen to your phone or computer like we have? Did your garage door open or remain locked without you initiating it? They sure do have a mighty toolbox. We’d love to hear your experiences, so please comment below the following articles:
Inside TAO: Documents Reveal Top NSA Hacking Unit
From Speigel
In January 2010, numerous homeowners in San Antonio, Texas, stood baffled in front of their closed garage doors. They wanted to drive to work or head off to do their grocery shopping, but their garage door openers had gone dead, leaving them stranded. No matter how many times they pressed the buttons, the doors didn’t budge. The problem primarily affected residents in the western part of the city, around Military Drive and the interstate highway known as Loop 410.
It was thanks to the garage door opener episode that Texans learned just how far the NSA’s work had encroached upon their daily lives. For quite some time now, the intelligence agency has maintained a branch with around 2,000 employees at Lackland Air Force Base, also in San Antonio. In 2005, the agency took over a former Sony computer chip plant in the western part of the city. A brisk pace of construction commenced inside this enormous compound. The acquisition of the former chip factory at Sony Place was part of a massive expansion the agency began after the events of Sept. 11, 2001. (Read the rest here.)
More Editor’s Notes – Here is another example of that mighty toolbox:
NSA’s ANT Division Catalog of Exploits for Nearly Every Major Software/Hardware/Firmware
From Leak Source
After years of speculation that electronics can be accessed by intelligence agencies through a back door, an internal NSA catalog reveals that such methods already exist for numerous end-user devices.
When it comes to modern firewalls for corporate computer networks, the world’s second largest network equipment manufacturer doesn’t skimp on praising its own work. According to Juniper Networks’ online PR copy, the company’s products are “ideal” for protecting large companies and computing centers from unwanted access from outside. They claim the performance of the company’s special computers is “unmatched” and their firewalls are the “best-in-class.” Despite these assurances, though, there is one attacker none of these products can fend off — the United States’ National Security Agency.
Specialists at the intelligence organization succeeded years ago in penetrating the company’s digital firewalls. A document viewed by SPIEGEL resembling a product catalog reveals that an NSA division called ANT has burrowed its way into nearly all the security architecture made by the major players in the industry — including American global market leader Cisco and its Chinese competitor Huawei, but also producers of mass-market goods, such as US computer-maker Dell. See: Cisco / Dell Comments Re: NSA Backdoors
These NSA agents, who specialize in secret back doors, are able to keep an eye on all levels of our digital lives — from computing centers to individual computers, from laptops to mobile phones. For nearly every lock, ANT seems to have a key in its toolbox. And no matter what walls companies erect, the NSA’s specialists seem already to have gotten past them.
This, at least, is the impression gained from flipping through the 50-page document. The list reads like a mail-order catalog, one from which other NSA employees can order technologies from the ANT division for tapping their targets’ data. The catalog even lists the prices for these electronic break-in tools, with costs ranging from free to $250,000.
(See the complete catalog and read more here.)
More Editor’s Notes – The following article compliments the previous article which if you go to that link exposes what Tyler Durden explains here: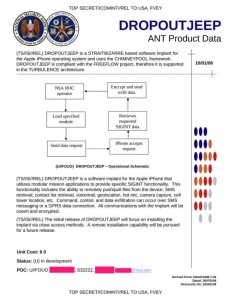
How The NSA Hacks Your iPhone – Presenting DROPOUT JEEP
From Zero Hedge’s Tyler Durden
Following up on the latest stunning revelations released yesterday by German Spiegel which exposed the spy agency’s 50 page catalog of “backdoor penetration techniques“, today during a speech given by Jacob Applebaum (@ioerror) at the 30th Chaos Communication Congress, a new bombshell emerged: specifically the complete and detailed description of how the NSA bugs,remotely, your iPhone.
The way the NSA accomplishes this is using software known as Dropout Jeep, which it describes as follows:
“DROPOUT JEEP is a software implant for the Apple iPhone that utilizes modular mission applications to provide specific SIGINT functionality. This functionality includes the ability to remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc. Command, control and data exfiltration can occur over SMS messaging or a GPRS data connection. All communications with the implant will be covert and encrypted.”
The flowchart of how the NSA makes your iPhone its iPhone is presented below:
- NSA ROC operator
- Load specified module
- Send data request
- iPhone accepts request
- Retrieves required SIGINT data
- Encrypt and send exfil data
- Rinse repeat
More Editor’s Notes – Finally for today’s post on the NSA, the New Yorker took a stab at explaining the recent report from the NSA Review Panel. Again, you be the judge:
INSIDE THE WHITE HOUSE N.S.A. REPORT: THE GOOD AND THE BAD
From John Cassidy at the New Yorker
On several occasions this year, I’ve criticized the Obama Administration for its obfuscations on intelligence matters and its overly defensive reaction to Edward Snowden’s revelations. At this stage, the President needs to fess up and say that the intelligence agencies went too far—a fact confirmed by Friday’s revelation, courtesy of Snowden’s documents, that the N.S.A. and C.G.H.Q., its British counterpart, have been snooping on international charities and aid groups, such as UNICEF, the United Nations’s children’s charity, and Médecins du Monde, a French humanitarian organization.
But a bit of credit where it is due. In commissioning an independent report on the National Security Agency’s activities, the White House didn’t follow the oft-used tactic of stuffing the outside review panel with yes men who could be relied upon to produce a whitewash—or, if it did, the ruse didn’t work. The report of the President’s Review Group on Intelligence and Communications Technologies, which came out on Wednesday, is lengthy and thoughtful. Its forty-six recommendations are, in some ways, surprisingly far-reaching. If fully enacted, they wouldn’t put an end to domestic surveillance. Far from it. But they would change how the N.S.A. operates, and, especially, how its activities are overseen.
Most of the news stories about the report restricted themselves to the executive summary, which is understandable. The rest of the report runs to nearly three hundred pages, and it covers a lot of complex areas. Its five authors were all experts on intelligence, constitutional law, or both: Richard A. Clarke, who served as the national coördinator for counter-terrorism in the administrations of Bill Clinton and George W. Bush; Michael J. Morell, a former deputy director and acting director of the Central Intelligence Agency; Geoffrey R. Stone, a law professor at the University of Chicago; Cass R. Sunstein, a Harvard law professor who served in the Clinton administration; and Peter Swire, another former Clinton official, who is now a professor at Georgia Tech.
Read the rest here, and further discussion here at the Guardian.


